Adding Firmware files Products
- May 5, 2023
- Posted by: vmelinje
- Category: Stock Firmware Download
As such, we’ll download and install the latest version before moving forward. Now click on the Auto button to start flashing the boot-loader to your https://www.k4craft.com/community/unlock-the-full-potential-of-your-sm-g925a-with/ printer.
- Software, on the other hand, is installed onto a device and used for interaction, such as browsing the internet, word processing, listening to music, and videoconferencing.
- Repetier is a solid, high-quality firmware with loads of features.
- The purpose of updating the firmware is to enhance the user experience without adding new features and minimize bug fixes and the need for device repairs.
Thank you so much and should I ever need attorney services down the road, I’ll certainly be a repeat customer. Get free proposals from vetted lawyers in our marketplace. Want to stay informed on the latest news in cybersecurity? Sign up for our newsletter and learn how to protect your computer from threats. Built In’s expert contributor network publishes thoughtful, solutions-oriented stories written by innovative tech professionals. It is the tech industry’s definitive destination for sharing compelling, first-person accounts of problem-solving on the road to innovation.
firmware to your computer to be able to use the nRF Sniffer for Bluetooth® LE. Step 8 Turn on your 3D printer, and complete the home-sequence if needed. This solution article explains how to make a custom .Hex (firmware) file. With bootloader is 621kb, which doesn’t make a lot of sense haha.
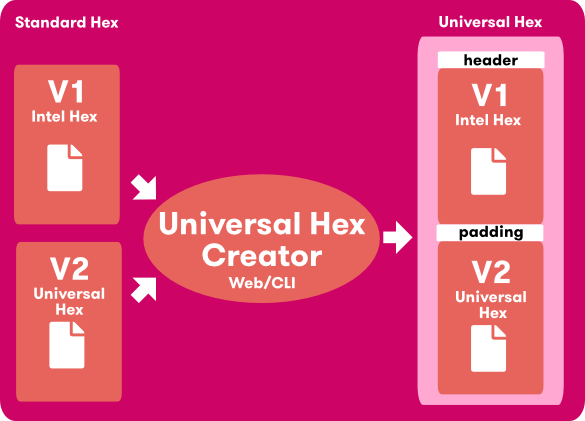
When you open the main editing window, you’ll notice that a new empty file has been created. The boxes that indicate where new data can be entered are colored lighter gray. When you enter a hex value, the corresponding character appears in the ANSI pane as well as the hex value. A straightforward and rather common task would be to replace a set of bytes.
FortiGuard intelligence helps discover and segment IoT devices, and enforces security policies against threats. It can also assign IoT devices to a network access control (NAC) solution through virtual local-area networks (VLANs), simplifying the management process in customer environments. Hardware devices are vulnerable to firmware attacks, which can lead to hackers embedding malware into the firmware. The BIOS has proven to be particularly insecure because different devices often share the same code, enabling attackers to discover and exploit common vulnerabilities. Then, applications are a big sets of instructions that perform specific tasks. American computer scientist Ascher Opler is said to have coined the phrase firmware in a 1967 issue of the publication Datamation. He used the term to describe a type of microprogram in between hardware and software.
